Cyber security
Cyber security threats
- Keeping data safe is extremely important for many reasons.
- Data can be corrupted or deleted either through accidental damage or malicious acts. There are also many ways data can be intercepted leading to cyber security threats. The following list shows the cyber threats which will be considered in this section:
- brute force attacks
- data interception
- distributed denial of service (DDoS) attacks
- hacking
- malware (viruses, worms, Trojan horse, spyware, adware and ransomware) »
- phishing
- pharming
- social engineering.
Brute force attacks
If a hacker wants to ‘crack’ your password, they can systematically try all the different combinations of letters, numbers and other symbols until eventually they find your password.
This is known as a brute force attack and there isn’t a lot of sophistication in the technique.
Check if the password is one of the most common ones used(the five most common are: 123456, password, qwerty, 111111 and abc123); since these simple passwords are seen so many times it’s a good place for the hacker to start.
If it isn’t in the common password list, the next thing to do is to start with a strong word list (this is a text file containing a collection of words that can be used in a brute force attack); some programs will generate a word list containing a million words. Nonetheless this is still a faster way of cracking a password than just total trial and error.
Data interception
Data interception is a form of stealing data by tapping into a wired or wireless communication link.
The intent is to compromise privacy or to obtain confidential information.
Interception can be carried out using a packet sniffer, which examines data packets being sent over a network.
The intercepted data is sent back to the hacker.
This is a common method when wired networks are used.
Wi-Fi (wireless) data interception can be carried out using wardriving (or sometimes called Access Point Mapping).
to safeguard against wardriving, the use of a wired equivalency privacy (WEP) encryption protocol, together with a firewall, is recommended.
Distributed Denial of Service (DDoS) attacks
A denial of service (DoS) attack is an attempt at preventing users from accessing part of a network, notably an internet server.
The attacker may be able to prevent a user from:
- accessing their emails
- accessing websites/web pages
- accessing online services (such as banking).
One method of attack is to flood the network with useless spam traffic.
In a distributed denial of service (DDoS) the spam traffic originates from many different computers, which makes it hard to block the attack.
Hacking
Hacking is generally the act of gaining illegal access to a computer system without the user’s permission.
This can lead to identity theft or the gaining of personal information; data can be deleted, passed on, changed or corrupted.
Malicious hacking, as described above, takes place without the user’s permission, and is always an illegal act.
However, universities and companies now run courses in ethical hacking.
This occurs when companies authorise paid hackers to check out their security measures and test how robust their computer systems are to hacking attacks.
Malware
- Malware is one of the biggest risks to the integrity and security of data on a computer system.
- There are many forms of malware; this chapter will only consider the following in any detail.
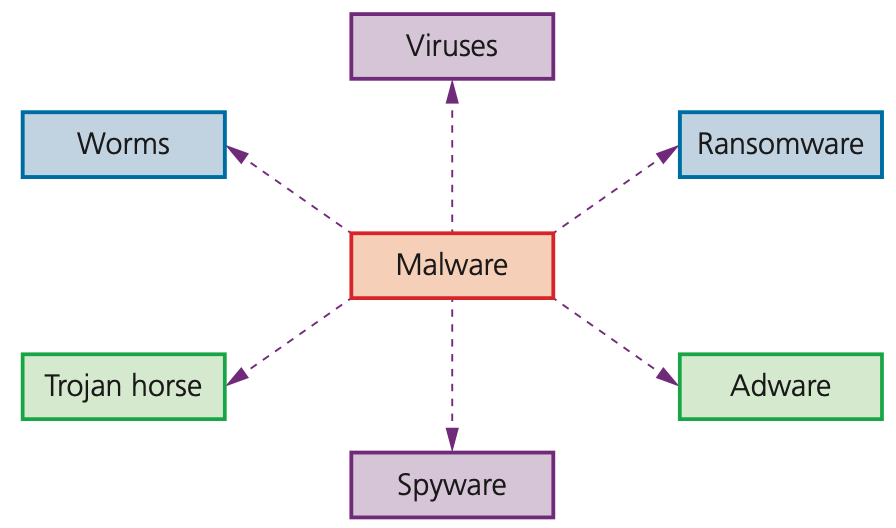
Viruses
Viruses are programs or program code that replicate (copies themselves) with the intention of deleting or corrupting files, or causing a computer to malfunction (for example, by deleting .exe files, filling up the hard drive with ‘useless’ data, and so on).
Viruses need an active host program on the target computer or an operating system that has already been infected, before they can actually run and cause harm (that is, they need to be executed by some trigger before starting to cause any damage).
Worms
Worms are a type of stand-alone malware that can self-replicate.
Their intention is to spread to other computers and corrupt whole networks; unlike viruses, they don’t need an active host program to be opened in order to do any damage.
They remain inside applications which allows them to move throughout networks.
Worms frequently arrive as message attachments and only one user opening a worm-infested email could end up infecting the whole network.
As with viruses, the same safeguards should be employed, together with the running of an up-to- date anti-virus program.
Trojan horse
A Trojan horse is a program which is often disguised as legitimate software but with malicious instructions embedded within it.
A Trojan horse replaces all or part of the legitimate software with the intent of carrying out some harm to the user’s computer system.
They need to be executed by the end-user and therefore usually arrive as an email attachment or are downloaded from an infected website.
Spyware
Spyware is software that gathers information by monitoring a user’s activities carried out on their computer.
The gathered information is sent back to the cybercriminal who originally sent the spyware.
They are primarily designed to monitor and capture web browsing and other activities and capture personal data.
Spyware can be detected and removed by anti-spyware software.
The big danger of spyware is the method it used to enter a user’s system and exploit it
Adware
Adware is a type of malware.
At its least dangerous it will attempt to flood an end-user with unwanted advertising.
For example, it could redirect a user’s browser to a website that contains promotional advertising, it could appear in the form of pop-ups, or it could appear in the browser’s toolbar and redirect search requests.
Although not necessarily harmful, adware can:
- highlight weaknesses in a user’s security defences
- be hard to remove – it defeats most anti-malware software since it can be difficult to determine whether or not it is harmful
- hijack a browser and create its own default search requests.
Ransomware
Essentially, ransomware are programs that encrypt data on a user’s computer and ‘hold the data hostage’.
The cybercriminal waits until the ransom money is paid and, sometimes, the decryption key is then sent to the user.
It has caused considerable damage to some companies and individuals.
This malware restricts access to the computer and encrypts all the data until a ransom is paid.
It can be installed on a user’s computer by way of a Trojan horse or through social engineering.
When ransomware is executed, it either encrypts files straightaway or it waits for a while to determine how much of a ransom the victim can afford.
Summary of malware
| Summary of malware |
|---|
| Viruses - programs (or program code) that can replicate/copy themselves with the intentiorof deleting or corrupting files, or causing the computer to malfunction. They need an activehost program on the target computer or an operating system that has already been infectedbefore they can run |
| Worms -- these are types of standalone viruses that can replicate themselves with theintention of spreading to other computers; they often networks to search out computers with weak security that are prone to such attacks |
| Trojan horses - these are malicious programs often disguised as legitimate software; theyreplace all or part of the legitimate software with the intent of carrying out some harm to theuser s computer system |
| Spyware - software that gathers information by monitoring, for example, all the activity ona user's computer; the gathered information is then sent back to the person who sent thesoftware (sometimes spyware monitors key presses and is then referred to as key loggingsoftware) |
| Adware - software that floods a user's computer with unwanted advertising; usually in theform of pop-ups but can frequently appear in the browser address window redirecting thebrowser to a fake website which contains the promotional adverts |
| Ransomware - programs that encrypt the data on a user's computer; a decryption key issent back to the user once they pay a sum of money (a ransom): they are often sent via aTrojan horse or by social engineering |
Phishing
Phishing occurs when a cybercriminal sends out legitimate-looking emails to users.
The emails may contain links or attachments that, when initiated, take the user to a fake website; or they may trick the user into responding with personal data (for example, bank account details or credit/debit card details).
Another term connected to phishing is spear phishing; this is where the cybercriminal targets specific individuals or companies to gain access to sensitive financial information or industrial espionage – regular phishing is not specific regarding who the victims are.
TIP
There are numerous ways to help prevent phishing attacks:
- be aware of new phishing scams
- not to click on any emails links unless totally certain that it is
- run anti-phishing toolbars on browsers
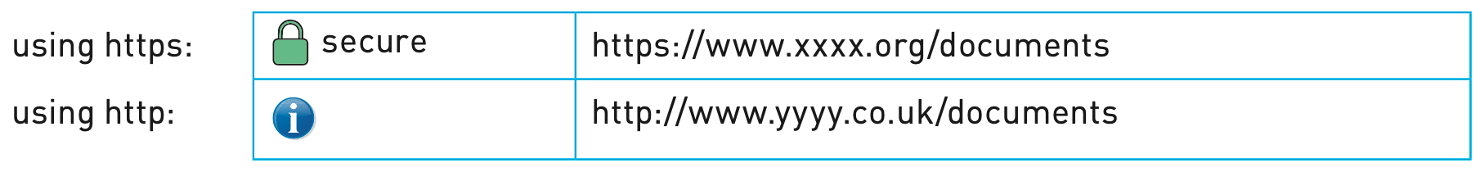
- look out for https or the green padlock symbol in the address bar
- regular checks of online
- ensure an up-to-date browser is running on the computer device and run a good firewall in the background at all times;
- be very wary of pop-ups and use the browser to block them;
Pharming
- Pharming is malicious code installed on a user’s computer or on an infected website.
- The code redirects the user’s browser to a fake website without the user’s knowledge.
- Unlike phishing, the user doesn’t actually need to take any action for it to be initiated.
- The creator of the malicious code can gain personal data, such as bank details, from the user.
- Often the website appears to come from a trusted source and can lead to fraud and identity theft.
DNS cache poisoning
- Every time a user types in a URL, their browser contacts the DNS server; the IP address of the website will then be sent back to their browser.
- However, DNS cache poisoning changes the real IP address values to those of the fake website; consequently, the user’s computer will connect to the fake website.
TIP
- It is possible to mitigate against the risk of pharming:
- Use of anti-virus software can detect unauthorised alterations to a website address and warn the user of the potential risks.
- However, if the DNS server itself has been infected (rather than the user’s computer) it is much more difficult to mitigate the risk.
- Many modern browsers can alert users to pharming and phishing attacks.
- It is very important to check the spelling of websites to ensure the web address used is correct.
- As with phishing, use of https or the green padlock symbol in the address bar is an additional form of defence
Social engineering
- Social engineering occurs when a cybercriminal creates a social situation that can lead to a potential victim dropping their guard.
- It involves the manipulation of people into breaking their normal security procedures and not following best practice.
- There are five types of threat that commonly exist
Access levels
- In many computer systems, user accounts control a user’s rights.
- This often involves having different levels of access for different people.
- When using databases, levels of access are particularly important; it is essential to determine who has the right to read, write and delete data, for example.
- By having different views of data tables, it is possible for different users to only have access to certain data.
- In this type of application, users are allowed to use privacy settings rather than passwords to decide the level of access.
Anti-malware
- Anti-spyware software detects and removes spyware programs installed illegally on a user’s computer system.
- The general features of anti-spyware are:
- detect and remove spyware already installed on a device
- prevent a user from downloading spyware
- encrypt files to make the data more secure in case it is ‘spied’ on
- encryption of keyboard strokes to help remove the risk posed by the
- keylogging aspects of some spyware
- blocks access to a user’s webcam and microphone (the software stops the spyware taking over the control of a user’s webcam and microphone which can be used to collect information without the user’s knowledge)
- scans for signs that the user’s personal information has been stolen and warns the user if this has happened.
Authentication
Authentication refers to the ability of a user to prove who they are.
There are three common factors used in authentication:
- something you know (for example, a password or PIN code)
- something you have (for example, a mobile phone or tablet)
- something which is unique to you (for example, biometrics).
There are a number of ways authentication can be done.
- Passwords and user names
- Biometrics
- Two-step verification
Passwords and user names
- Passwords are used to restrict access to data or systems.
- run anti-spyware software to make sure that your passwords aren’t being relayed back to whoever put the spyware on your computer
- change passwords on a regular basis in case they have come into the possession of another user, illegally or accidentally
- passwords should not be easy to crack (for example, your favourite colour, name of a pet or favourite music artist); passwords are grouped as either strong (hard to crack or guess) or weak (relatively easy to crack or guess)
- strong passwords with numbers, letters and symbols
Biometrics
- Biometrics can be used in much the same way as passwords as a way of identifying a user.
- Biometrics relies on certain unique characteristics of human beings; examples include:
- fingerprint scans
- retina scans
- face recognition
- voice recognition.
| Biometric technique | Benefits | Drawbacks |
|---|---|---|
| fingerprint scans | it is one of the most developed biometric techniques very easy to use relatively small storage requirements for the biometric data created | for some people it is very intrusive, since it is still related to criminal identification |
| it can make mistakes if the skin is dirty or damaged (e.g. cuts) | ||
| retina scans | very high accuracy there is no known way to replicate a person’s retina | it is very intrusive it can be relatively slow to verify retina scan with stored scans very expensive to install and set up |
| face recognition | non-intrusive method relatively inexpensive technology | it can be affected by changes in lighting, the person’s hair, change in age, and if the person is wearing glasses |
| voice recognition | non-intrusive method verification takes less than 5 seconds relatively inexpensive technology | a person’s voice can be easily recorded and used for unauthorised access low accuracy an illness such as a cold can change a person’s voice, making absolute identification difficult or impossible |
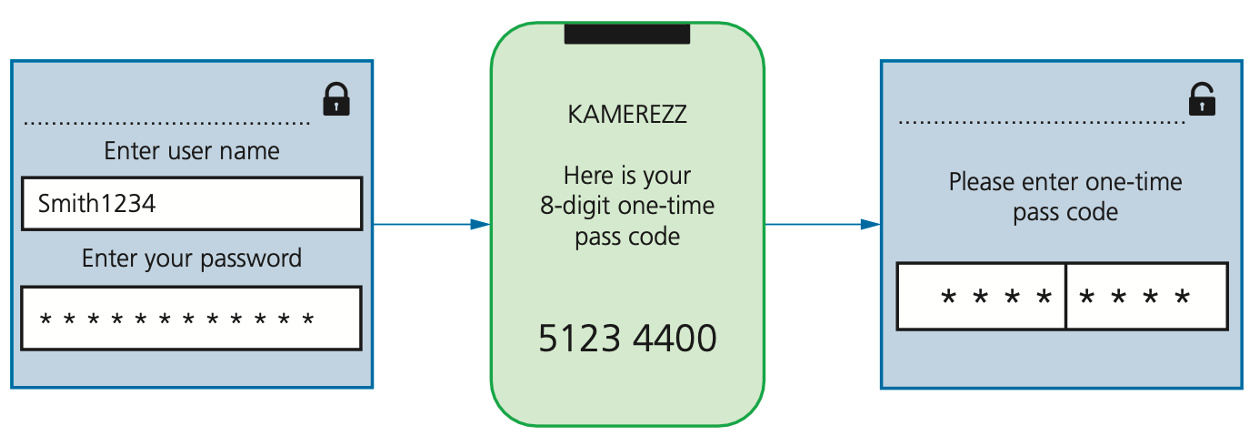
Two-step verification
- Two-step verification requires two methods of authentication to verify who a user is.
- It is used predominantly when a user makes an online purchase using a credit/debit card as payment method.
- For example, suppose Kate wishes to buy a new camera from a website. She logs into the website using her computer.
- This requires her to enter a user name and a password, which is step 1 of the authentication process.
Automatic software updates
Automatic software updates mean software on computers and mobile phones/ tablets is kept up-to-date.
Sometimes this is done overnight or when you log off the device.
These updates are vital since they may contain patches that update the software security (to protect against malware) or improve the software performance (for example, removal of bugs and addition of new features).
Checking the spelling and tone of communication and URL links
When emails are sent to you, there are three actions you always need to take before opening them or activating any links in them.
- Check out the spellings in the email and in the links; professional, genuine organisations will not send out emails which contain spelling or major grammatical errors (for example, Amazzon.com)
- Carefully check the tone used in the email message; if it is rushing you into doing something or if the language used seems inappropriate or incorrect, then it could be a phishing email or worse.
This is known as typo squatting where names close to the genuine names are used to fool you.
- www.gougle.com
- www.amozon.com
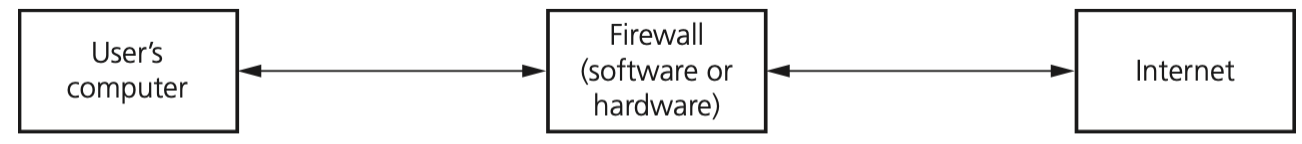
Firewalls
- A firewall can be either software or hardware.
- It sits between the user’s computer and an external network (for example, the internet) and filters information in and out of the computer.
- This allows the user to decide whether or not to allow communication with an external source and it also warns a user that an external source is trying to access their computer.
- Firewalls are the primary defence to any computer system to help protect it from hacking, malware (viruses and spyware), phishing and pharming.
WARNING
- The main tasks carried out by a firewall include:
- to examine the ‘traffic’ between user’s computer (or internal network) and a public network (for example, the internet)
- checks whether incoming or outgoing data meets a given set of criteria
- if the data fails the criteria, the firewall will block the ‘traffic’ and give the user (or network manager) a warning that there may be a security issue
- the firewall can be used to log all incoming and outgoing ‘traffic’ to allow later interrogation by the user (or network manager)
- criteria can be set so that the firewall prevents access to certain undesirable sites; the firewall can keep a list of all undesirable IP addresses
- it is possible for firewalls to help prevent viruses or hackers entering the user’s computer (or internal network)
DANGER
- However, there are certain circumstances where the firewall can’t prevent potential harmful ‘traffic’:
- it cannot prevent individuals, on internal networks, using their own hardware devices (e.g. modems, smartphones) to bypass the firewall
- employee misconduct or carelessness cannot be controlled by firewalls (for example, control of passwords or user accounts)
- users on stand-alone computers can choose to disable the firewall, leaving their computer open to harmful ‘traffic’ from the internet.
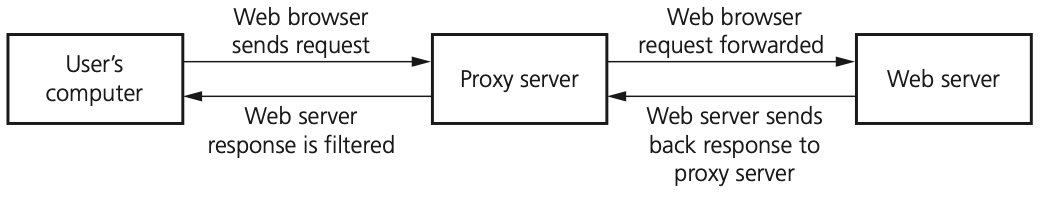
Proxy servers
- Proxy servers act as an intermediate between the user and a web server
- allows internet traffic to be filtered; it is possible to block access to a website if necessary
- keeps users’ IP addresses secret which improves security
- if the internet traffic is valid, access to the web server is allowed
- if the internet traffic is invalid, access to the web server is denied
- it is possible to block requests from certain IP addresses
- prevents direct access to a web server by sitting between the user and the web server
- if an attack is launched, it hits the proxy server instead – this helps to prevent hacking, DoS, and so on
- used to direct invalid traffic away from web servers which gives additional protection
- by using the feature known as a cache, it is possible to speed up access to information/data from a website;
- proxy servers can also act as firewalls.
Privacy settings
- Privacy settings are the controls available on web browsers, social networks and other websites that are designed to limit who can access and see a user’s personal profile. They were discussed earlier in the section on access rights. Privacy settings can refer to:
- a ‘do not track’ setting; the intention here is to stop websites collecting and using browsing data which leads to improved security
- a check to see if payment methods have been saved on websites; this is a useful safety feature which prevents the need to type in payment details again
- safer browsing; an alert is given when the browser encounters a potentially dangerous website
- web browser privacy options
- website advertising opt-outs;
- apps; for instance, the sharing of location data in map apps can be switched off.
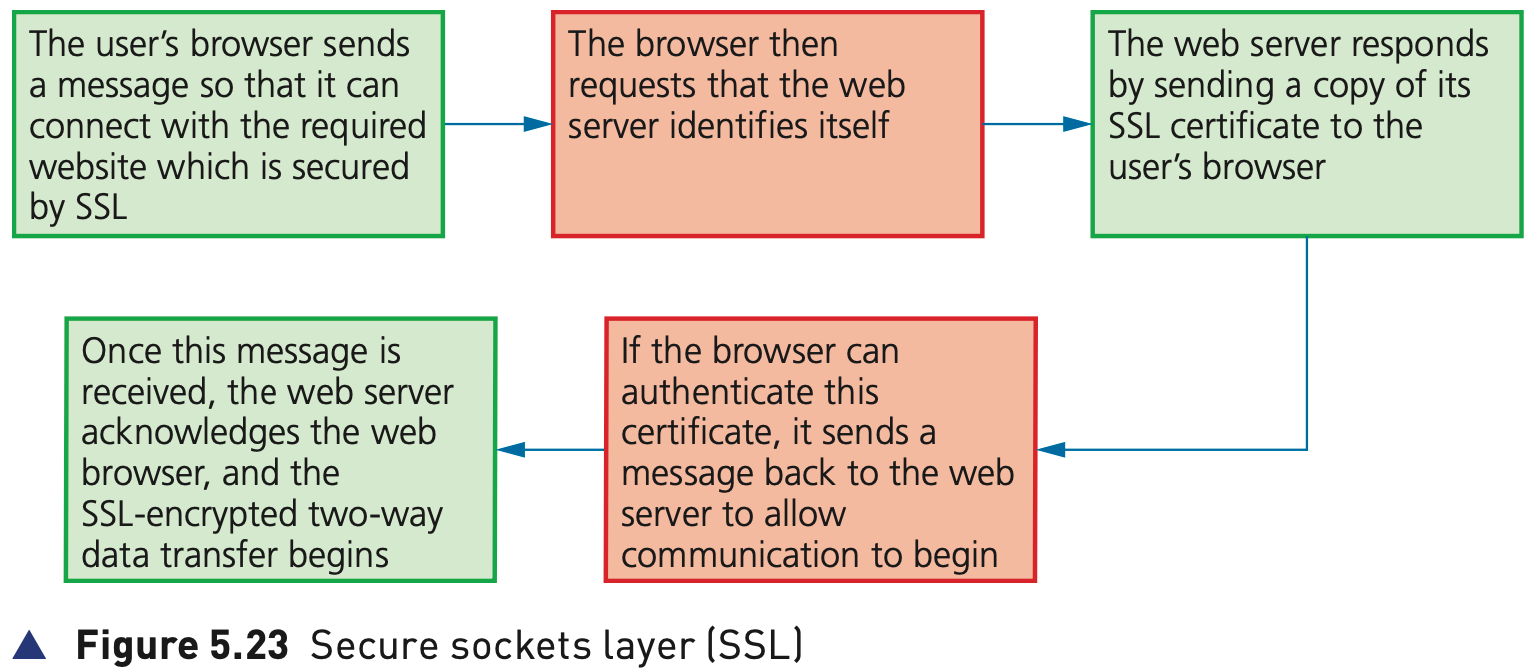
Secure Sockets Layer (SSL)
- Secure Sockets Layer (SSL) is a type of protocol – a set of rules used by computers to communicate with each other across a network. - This allows data to be sent and received securely over the internet.
- When a user logs onto a website, SSL encrypts the data – only the user’s computer and the web server are able to make sense of what is being transmitted. A user will know if SSL is being applied when they see https or the small padlock in the status bar at the top of the screen.
- The address window in the browser when https protocol is being applied, rather than just http protocol, is quite different